Cyber Security Practice Mckinsey

The institute of international finance iif and mckinsey co.
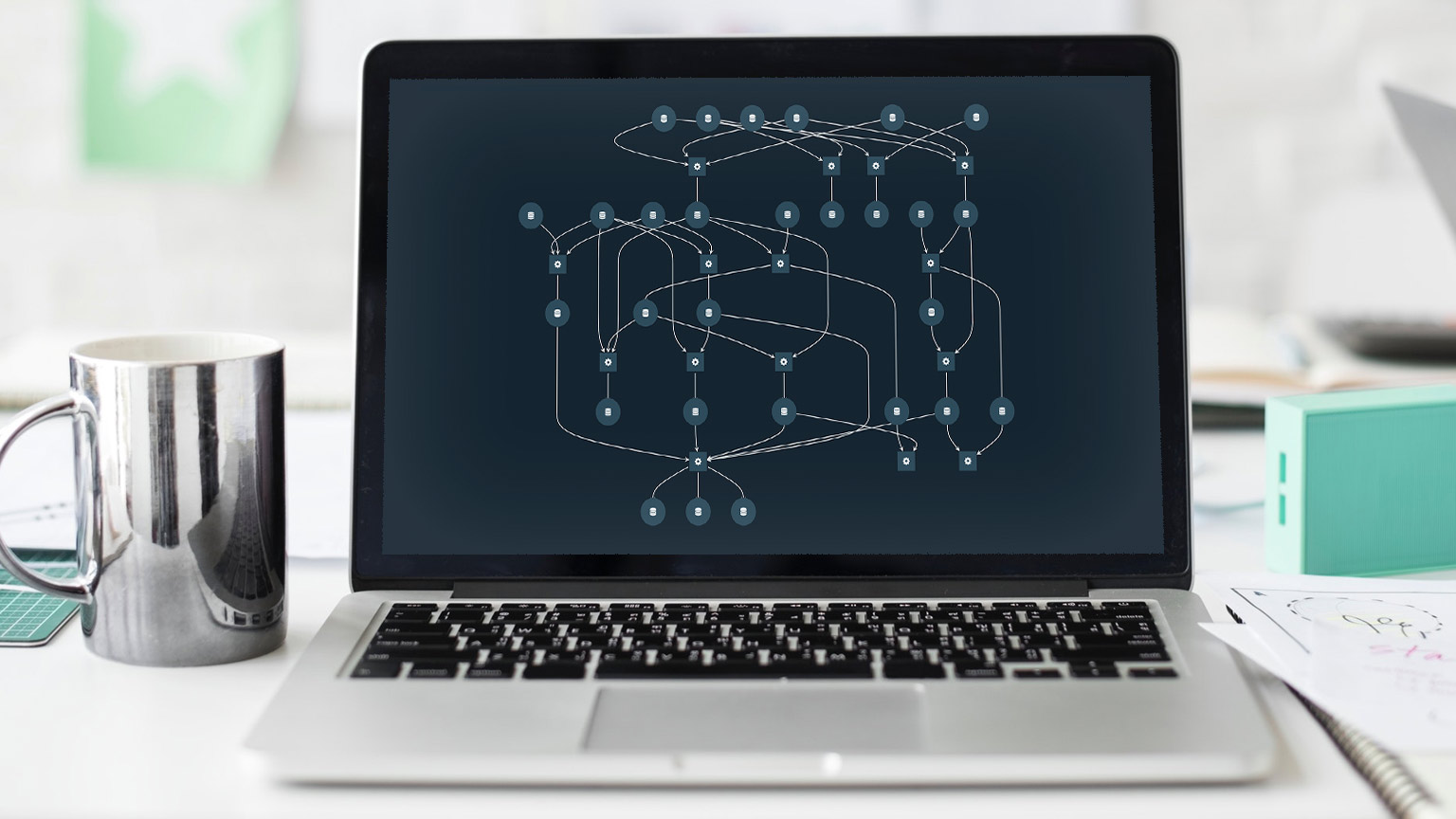
Cyber security practice mckinsey. It is an integrated decision support system creating visibility on all relevant assets end user devices applications infrastructure networks and buildings. Convert cyber into a long term competitive advantage. Please email us at. You will help mckinsey develop our expertise in this area and you ll have the opportunity to shape this fast growing initiative.
This article is advancing a risk based approach to cybersecurity which means that to decrease enterprise risk leaders must identify and focus on the elements of cyberrisk to target. At company after company fundamental tensions arise between the business s need to digitize and the cybersecurity team s responsibility to protect the organization its employees and its customers within existing cyber operating models and practices. Include cybersecurity in management and governance processes. 27 globally active firms participated in the survey and more than 50 companies.
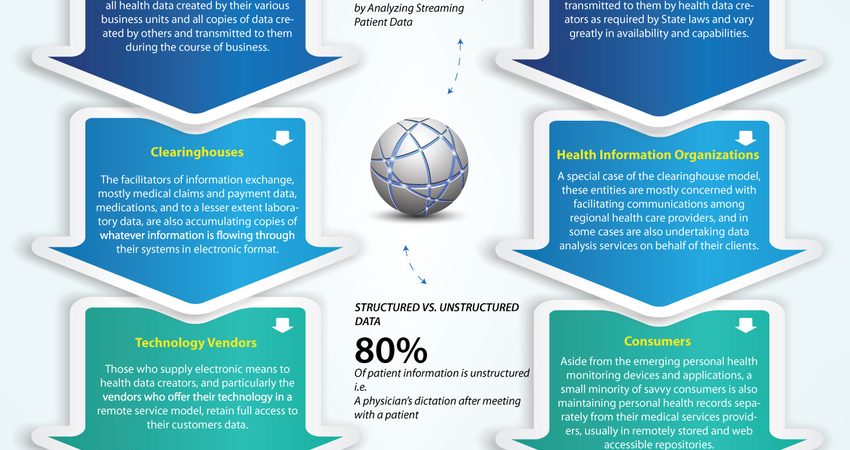
Organization wanted to understand how its technical security architecture and capabilities compared against best practice controls used among cross industry security leaders. Cyber risk is a complex nonfinancial issue with the power to erode a company s bottom line and brand value. The survey was designed to provide an understanding of current and. Please email us at.
The following seven practices are essential to achieving digital resilience. The cybersecurity team can anticipate and embed needed security capabilities at the right level of maturity by working with business partners. A recent joint survey on cyber resilience by the institute of international finance iif and mckinsey found significant concerns regarding third party security and our survey determined that 33 percent of financial services firms do not have proper vendor remote access management with multifactor authentication controls. Have completed a joint survey and research project around cyber resilience to provide an understanding of current and planned practices that financial firms are undertaking to enable and strengthen firm level and sector level cyber resilience.
Given the reluctance of employees to embrace security controls it is essential that top executives starting with the ceo spread the message that cybersecurity is not only critical to the company s ability to do business but also a powerful business enabler. Our risk practice supports clients facing challenges developing and implementing tailored concepts for risk recognition measurement and control. Proven experience in cyber security strategy and risk based.