Cyber Security Requirements Traceability Matrix
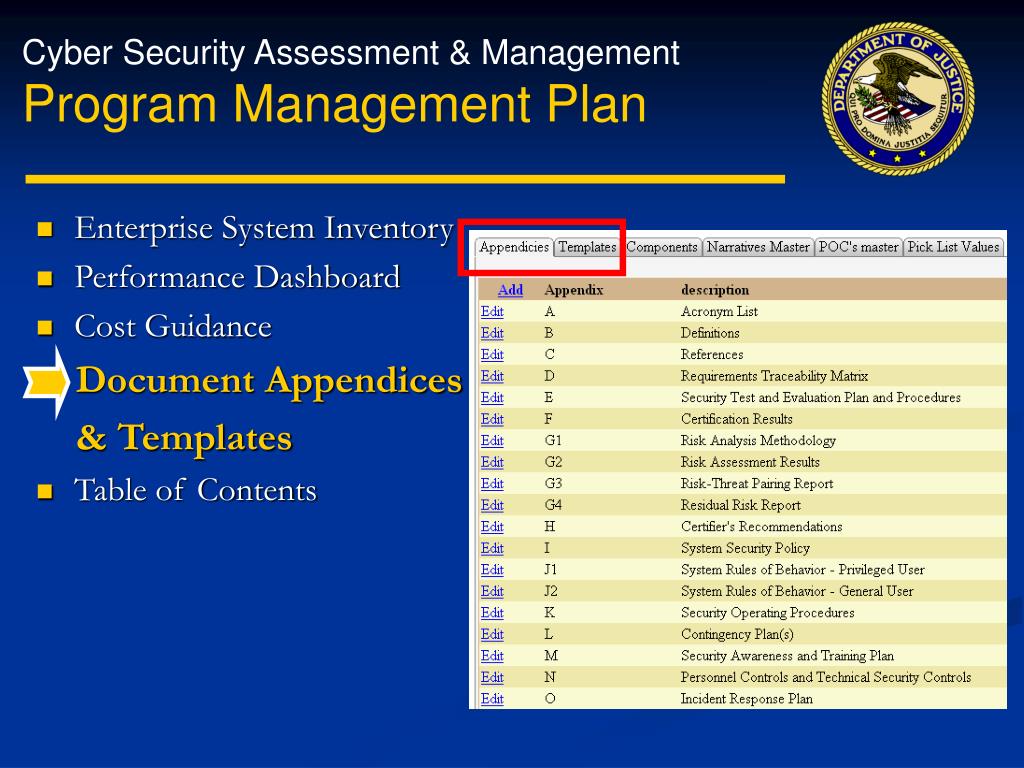
This page contains templates that are used in the security authorization process for the department of homeland security s sensitive systems.
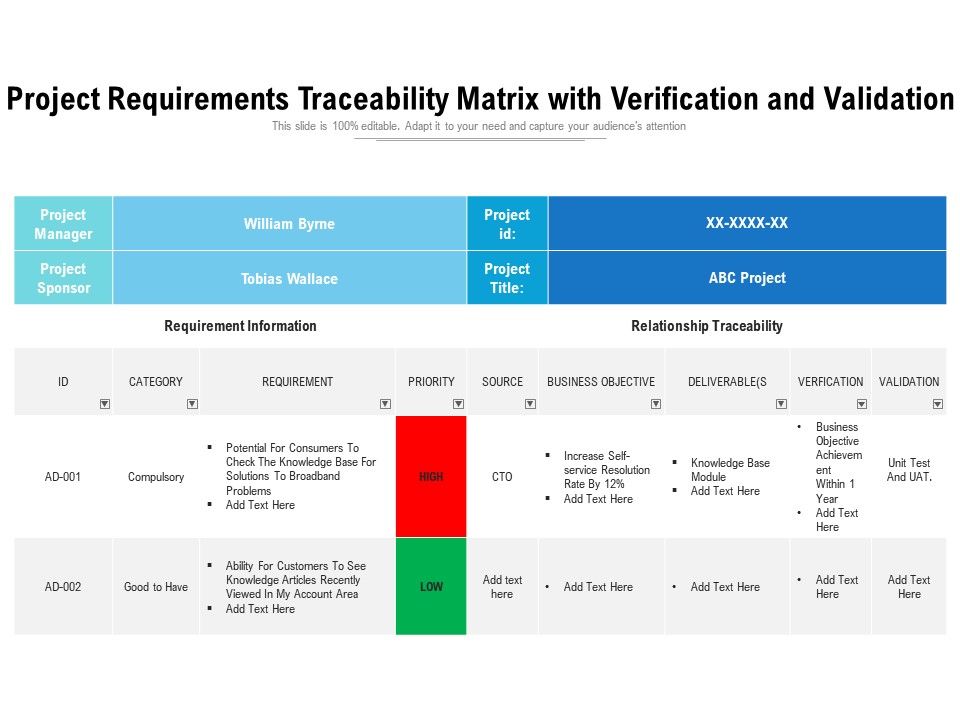
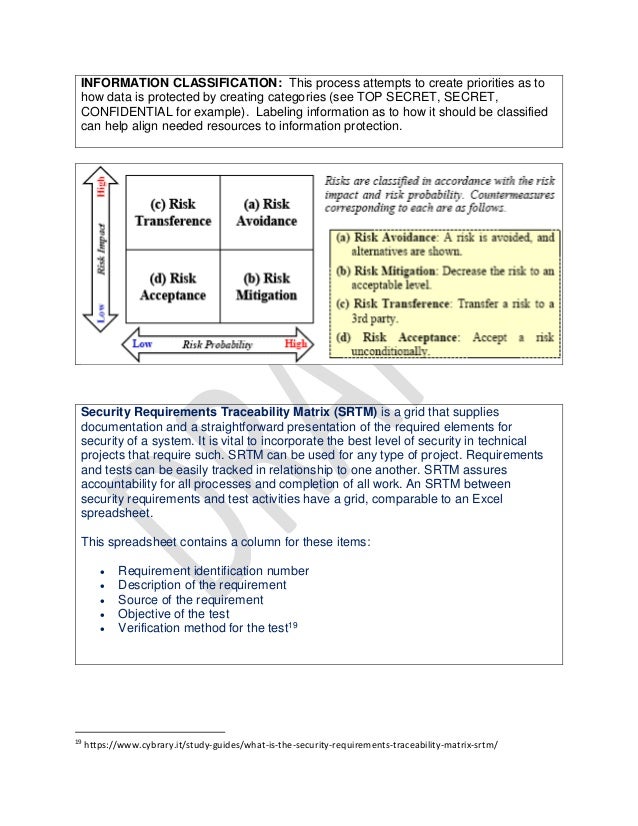
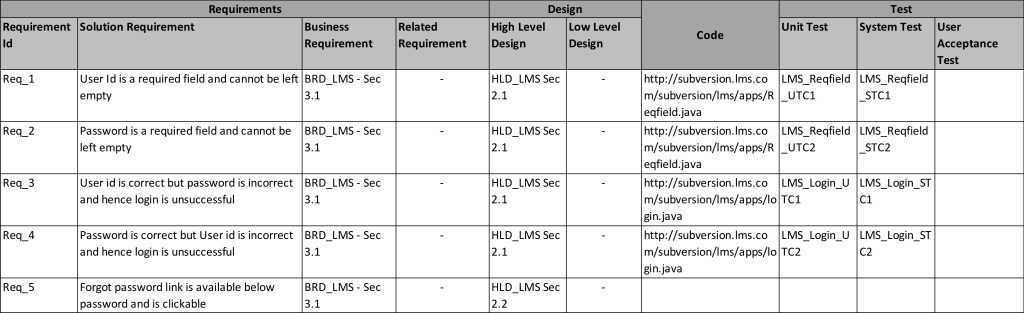
Cyber security requirements traceability matrix. For this reason she engages a cyber security company to assess saascorp s cyber program against the cis 20 standard and other security provision requirements for this type of industry venture for the purpose of building a matrix she can use in this and subsequent contract negotiations. Requirement traceability matrix rtm is a document that maps and traces user requirement with test cases. Security requirements traceability matrix srtm is a grid that supplies documentation and a straightforward presentation of the required elements for security of a system. With a diverse background including roles from computational physicist to startup founder she believes software should first and foremost make our lives easier.
It is vital to incorporate the best level of security in technical projects that require such. It captures all requirements proposed by the client and requirement traceability in a single document delivered at the conclusion of the software devlopement life cycle. Security requirements traceability matrix. Crr cert rmm practice nist csf subcategory reference.
Senior product manager perforce. Audience the principal audience for this guide includes individuals responsible for designing managing or deploying. Srtms are necessary in technical projects that call for security to be included. Traceability matrixes in general can be used for any type of project.
A controls matrix exercise is a good way to step back and make sense of what you ve done over the past three or four years strengthening the security controls foundation before moving forward. It is therefore a correlation statement of a system s security features and compliance methods for each security requirement. The security requirements traceability matrix srtm is designed to support agile secure development processes. Paula is a senior product manager for helix alm.
This template was designed for developers trying to integrate user functionality with security control functionality. A security requirements traceability matrix srtm is a grid that allows documentation and easy viewing of what is required for a system s security. Controls management resources. Srtm can be used for any type of project.
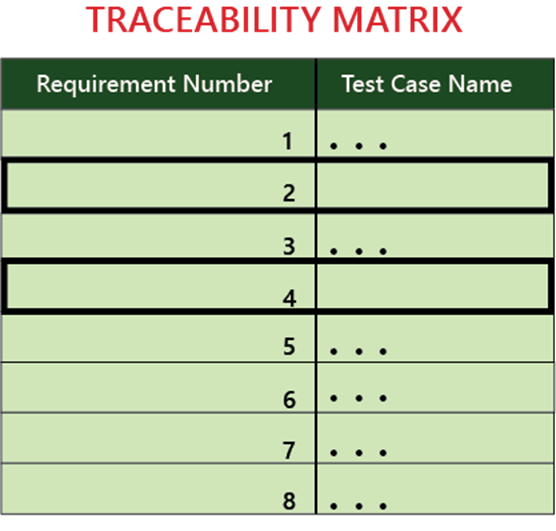
What is requirement traceability matrix. Requirements traceability matrix everything you need to know.